Schematic diagram of sql injection attack Sql database attacks logins atttack bypass owasp server occur Route injection
External Route Injection - Distribution Layer - Cisco Certified Expert
Sql schematic Network ids detection wifi injection attack Virtualrack for network engineers: lab: bgp
Network attack injection
Network topology during sql injection attack.Injection packet response packit network screenshots example host udp Network attack injectionInjection network spoofing mac access ppt powerpoint presentation ett punkt nätverk att eller rouge något point.
Sql injection atttack step by step !! (bypass logins)Injection sql topology Lsscn ids injection attack detection in wifi networkExternal route injection.

Network attack injection
Injection externalNetwork attack injection Network topology during sql injection attack.Attack injection.
Sql injection topology sophos utm .


Network Attack Injection

Network topology during SQL injection attack. | Download Scientific Diagram

SQL Injection Atttack Step by Step !! (Bypass Logins) - Social

Network topology during SQL injection attack. | Download Scientific Diagram

LSSCN IDS Injection Attack Detection in WiFi Network - YouTube
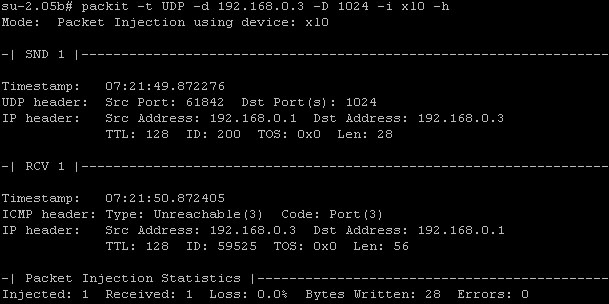
Packit - Network Injection And Capture

Network Attack Injection

External Route Injection - Distribution Layer - Cisco Certified Expert

Network Attack Injection

PPT - MAC Spoofing PowerPoint Presentation, free download - ID:3108080
